Lawful Interception Suite (LI Suite) for Packet Data Network
Decision Group’s Lawful Interception Suite (LI Suite) for Packet Data Network provides all the hardware and software needed for targeted network surveillance based on a court-issued warrant. The suite includes iMediator, iMonitor, our EDDM module that decodes and reconstructs network packets, and the evidence archiving manager – Data Retention Management System.
These devices are integrated to create a powerful tool for the law enforcement community and their efforts to eliminate cybercrime.
When deploying a Lawful Interception system, there are three important factors to consider: the devices, the telecom/ISP interception point, and the warrant that issued by a court and authorizing the legal interception of a suspect’s network traffic.
When the warrant is issued by the court, the warrant information is entered into Decision Group’s iMonitor. The iMonitor then sends the warrant information as HI1 data to the iMediator device that is located within the telecom/ISP network. This target provision information is then sent to the ISP’s AAA and Broadband Remote Access Server (B-RAS).
When the target accesses the internet through the telecom/ISP the AAA and B-RAS mirror the traffic and send the copy of the traffic to the iMediator by 2 types of data stream: X2 and X3. The X2 traffic that is sent to iMediator is the Interception Related Information, and the X3 traffic is the Content data.
These two data sets are returned to the iMonitor in the law enforcement domain by the standardized form: HI2 and HI3 respectively, where the HI3 data is correlated with HI2 and sent to the EDDM module for decoding and reconstruction. After the data has been decoded, it will then be sent to the Data Retention Management System where analysis and/or archiving will take place (Figure 1).
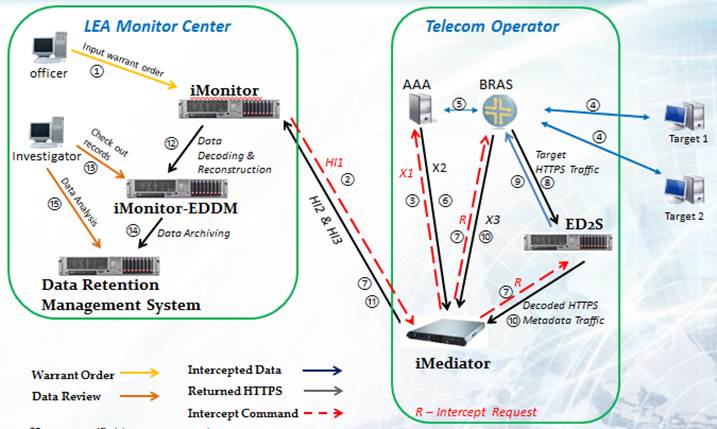
Figure 1 - Deployment of Decision Group's LI Suite in a Fixed Network
The main user interface for our Lawful Interception Suite is the iMonitor. Three user authorities exist for the iMonitor: Administrator, Operator, and Claimer. The Administrator has the authority to configure the system, create users, and enter warrant information. The Operator is restricted to only entering warrant information. The Claimer is the only authorized user to view the intercepted data.
Figure 2 is a view of the iMonitor user interface in the Operator authority, the Operator can create and view warrant information, but does not have access to system settings, or intercepted data.
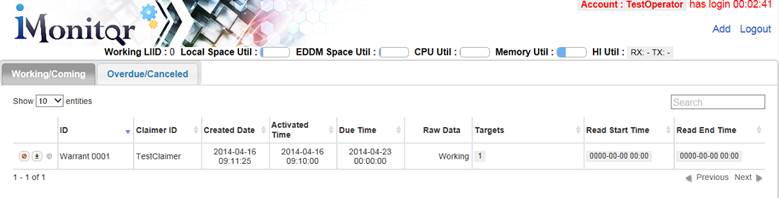
Figure 2 - iMonitor Operator authority User Interface
Figure 3 displays the iMonitor user interface in the Claimer authority.
Note that the Claimer authority can only view the intercepted data.
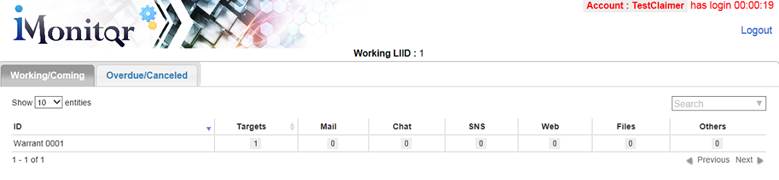
Figure 3 - iMonitor Claimer authority User Interface
More information about the DRMS can be found at: http://www.edecision4u.com/drms.html
Decision Group offers the devices, customization, training, and consulting needed in order to provide our partners with all the tools they need to be a full-spectrum LI solutions provider. For more information, contact Decision Group at: decision@decision.com.tw
For more information, subscribe to our YouTube channel: https://www.youtube.com/channel/UCFbnogK6juLEI5PhUp9Ib8A
To stay up to date on all our new products and service, please follow us on LinkedIn:
http://www.linkedin.com/company/decision-group
|