|
Telco and ISP Mass
Interception and Lawful Interception
Illegal or unauthorized Internet usage has increased in recent
years due to open communications policy in many countries all
over the world. The initial effort to prevent, curb and detect
these illegal usage activities by using content filtering and
application or service blocking solutions have failed as there
are too many back door paths. Terrorists start to love the
Internet and exploit all possible way of communications among
themselves through the Internet. Politicians start to make use
of Internet to spread their propaganda and message to their
supporters. Illegal betting organizations make use of Internet
for illegal transactions. Drugs and weapons dealers exploit the
Internet to close on drug and weapons smuggling deals. School
and universities students download unauthorized MP3s, Movies and
Software from the Internet. More and more people start to make
use of Internet for their own benefits in all sorts of ways. The
“Online Population?has increased tremendously in recent years.
The concern here is that are we closing our eyes on allowing
such kind of illegal, unauthorized or safety threatening
activities transmitted over the Internet? What is the best way
to detect such kind of activities? It is only through
comprehensive detection, alert and monitoring, we can prevent
disastrous incident from happening therefore defend the civilian
and national security.
The proposed solution to detect and counter such kind of act is
to deploy Internet Lawful Interception at Telco or ISP networks.
By deploying such kind of solution, all activities of Internet
subscribers (at office or at home) with actual content can be
monitored. Alert and notification rules by key words, file
extension, parameter or condition can be set. Once the
communication content matches the rules defined, immediate alert
can be sent by Email or SMS to the related lawful agencies.
Advanced analysis on the specific content like source (sender),
destination (receiver), IP address, possible location etc can be
carried out. These suspicious contents can also be archived, and
in case the culprit is brought to the court, all evidence
collected can be used. Furthermore, such kind of solution can
assist in early detection of possible terrorist activities and
prevent them to carry out such kind of action that can cause
violence and loss of human life.
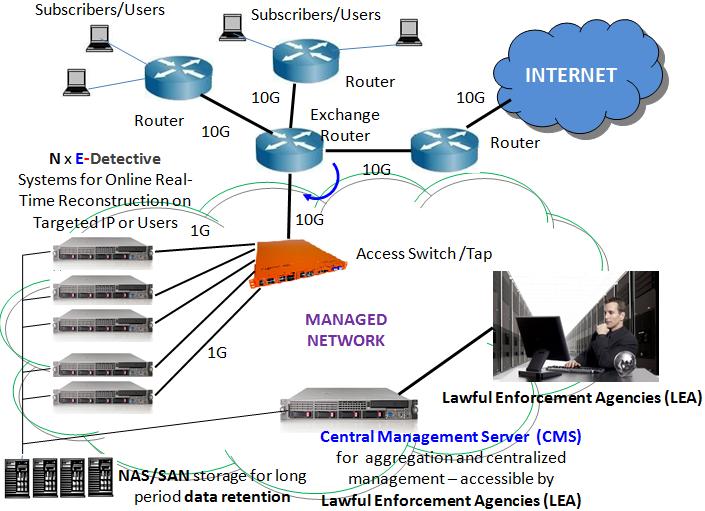
Diagram on the next page shows the Telco/ISP Lawful Interception
Solution provided by Decision Computer Group. This solution
consist of one advanced tap/access switch which collect traffic
from the ISP network (exchange) and split the traffic by IP
domain (or type) basis to multiple E-Detective (ED) systems for
online or on-the-fly decoding and reconstruction. E-Detective
systems will immediately reconstruct the collected traffic back
to its original content format. The supported protocols include:
Email (POP3, SMTP and IMAP), Webmail (Yahoo Mail,
Hotmail-Windows Live Mail, Gmail etc.), File Transfer (FTP and
P2P), Online Games, IM/Chat (Yahoo, MSN, ICQ, AOL, QQ, IRC,
Google Talk TW, Skype Voice Call Log), HTTP (Link, Content,
Reconstruct, Upload/Download, Video Stream) and Telnet. A
Centralized Management Server (CMS) will be used to manage all
E-Detective systems deployed. Besides, a PCAP Collector can
also be used to store the raw data traffics. The raw data
traffic can be analyzed further by exporting it into the
E-Detective Decoding Centre (EDDC) for offline reconstruction.
SAN and NAS can be used to keep or store for long term the
reconstructed data from all E-Detective systems or from PCAP
Collector or the EDDC systems.
Back to News
|