|
|
|
 |
 |
Current Telecom Market |
|
- More New Banks Emerging with Higher Competition in the Market, and M&A Happened Frequently
- Cheaper and Cheaper Interest Rate vs Higher and Higher OPEX in Bank Management
- Higher Risk due to Advanced Technologies, such as Internet Banking, Introduced into Market
- Global and Country Regulations, such as Basel-II, GLBA, Country Finance Auditing System, Restrictions of Regional Finance Organization, such as WMF…etc
- Compliance with Sarbine-Oxley Act to Prevent from Insider Transaction
- ISO 27001/BS7799 for Internal IT Security Auditing
|
 |
Major Issues in Bank |
|
- Gain Customer Confidence
- How to Retain Existing Customer and Increase Customer Contribution
- How to Attract More New Customer by Active Promotion Program
- Mitigate Risk in the Transaction and Business Processes
- How to Set up Common Standards to all Different Applications and Platforms inside Bank
- How to Adjust to More and More Auditing Reports from Country Finance Auditing Agency
- Put all IT Applications, Transactions, Infrastructure under Good Auditing
- How to Build up a Common IT Security Standard and Centralized Management inside Bank Organization
- Keep client information privacy under GLBA
|
 |
Customer Relation Management |
|
- Customer Behavior Analysis from Internet or Mobile Banking System
- Collect the Information of Customer Contribution by Integrating all Customer Transactions
- Collaborated Finance Service Promotion for Target Customers
- Primary Data Output to Report (Crystal Report) System, or Data Mining (Oracle, SAP, Teradata, SAS…etc) for Further Analysis
|
 |
Risk Management |
|
- Mandatory by Basel II
- Risk Assessment on all Business Processes
- Keep all Original Transaction Data, such as email, VoIP phone record, IM…etc, in Archive for Auditing Purpose for 3 to 5 Years
- Clear and Standard Format Report for Country Finance Monitoring and Auditing Organization
|
 |
DG E-Detective |
|
 |
| |
Decision Group E-Detective Tactic System |
| |
● VoIP Monitoring & Behaviour Analysis |
| |
> Solution for Telecom Service Providers:
- VoIP Monitoring/Network Behavior Recording
- Auditing and Record Keeping
- Data Retention and Archiving
|
 |
Major Features |
|
- Real-time Internet Interception, Monitoring System that Captures, Decodes and Reconstructs VoIP data and Various Types of Internet Traffic
- Compliance with Many Standards like Sarbanes Oxley Act (SOX), GLBA, SEC, NASD, ETSI, CALEA, ISO 27001…etc
- Free Text Search (search by Key Words with Boolean support), Conditional Search, Similar Search and Association with Relationship Search
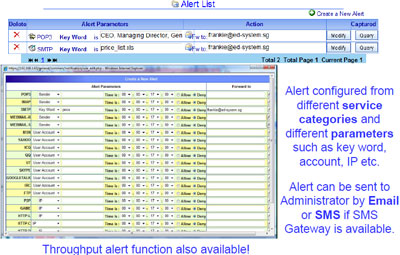
- Alert and Notification (Throughput, Conditional and Key Words Alert) Functions for User Behavior Analysis
- IP Tracking on Outbound and Inbound Messages
- Open ODBC Interface with Report System (Crystal Report) or Data Mining/Warehouse (Oracle or Teradata) or BI tools
|
 |
User Behavior |
|
- Summary Screen on Service Type, Frequency/Quantity, Throughput/Volume
- Daily Report on Data Volume in Different Time Slot
- Internet Content Usage Information Collection
- Prevention of dispute between customers and banks by proofing it with captured records
- All data can be retrieved by 3rd party solutions, such as Crystal Report, Oracle, SAP, SAS, Teradata…etc, for Further Analysis
|
 |
Behavior Report |
|
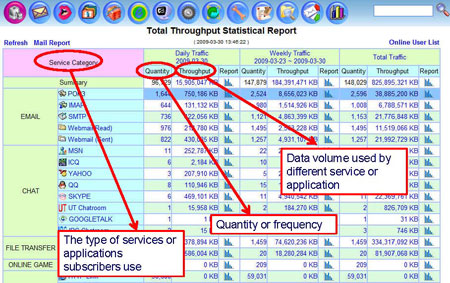 |
 |
Usage Report |
|
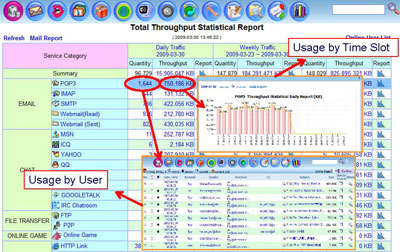 |
 |
Webpage Content Collection |
|
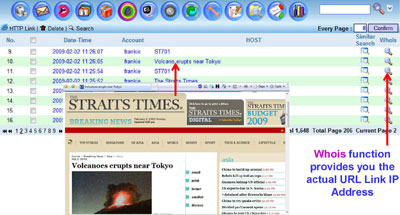 |
 |
Transaction Record By Email |
|
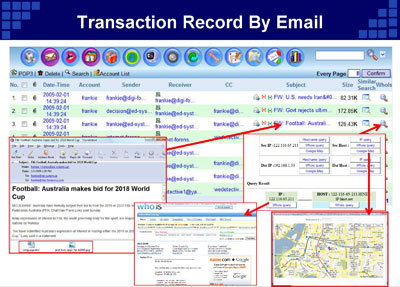 |
 |
Risk Management |
|
Instant Messaging Risk Management
- Original Email Data Retention
- Retain the original email data from outside network, so no one can revise it for evidence destruction and hidden (Required by SEC and Finance Auditing Agency)
- Key Word Searching on Archiving Email Data
- Open Interface for Risk Management Tools
- Standard report format provided
- Open ODBC Interface with 3rd party Risk Analysis system
|
 |
IM -Yahoo, MSN, ICQ, IRC, QQ, GTalk etc… |
|
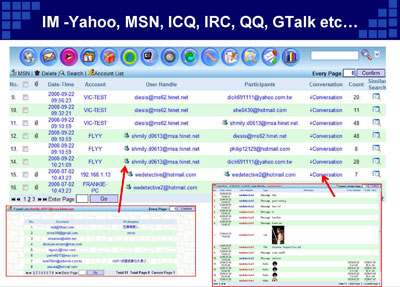 |
 |
IT Security |
|
Prevention of Data Leakage through Internet Detection of Keyword Leakage by Notification and Alert Build up Common IT Security Standard among Head Quarter and Branch offices
- Data Leakage Prevention inside Intranet
- Daily Report on User Usage Report
- Internal Internet Usage Control against Pornography and Gambling, Drug Dealing
|
|
|
 |
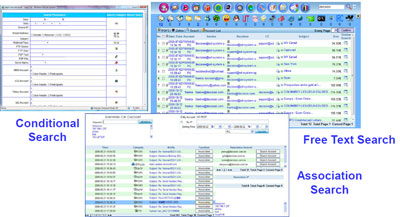
Search – Free Text, Condition, Association |
|
Complete Search – Free Text Search, Conditional Search, Similar Search
and Association Search |
|
 |
 |
Alert and Notification – Alert with Content |
|
 |
 |
Other Features |
|
- Support 1.2 Gbps bandwidth throughput
- Distributed Deployment with Central Management System in Data Centers of Head Quarter and Regional Hub through Intranet
- Support close to 150 protocols or services
- Backup function allows user to backup the captured raw data files or reconstructed contents.
- Functions available are Bookmark, Capture File List (Comparing the content of two files), Online IP List, Authority Assignment, Syslog Server … etc
|
 |
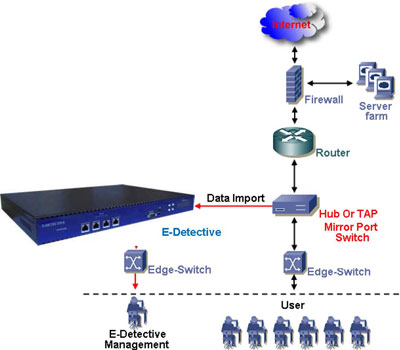
E-Detective for Risk Management |
|
All data packets on Ethernet are broadcast to everywhere, i.e., all physical signals will come to network Interface card of our appliance. NIC can be under promiscuous mode, so it can receive all data no matter what the MAC address it is. This is what the basic of Sniffer it is. |
|
 |
 |
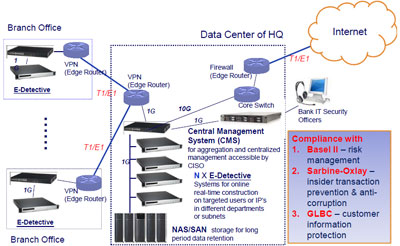
Data & Network Protection inside Bank |
|
 |
 |
Advantages |
|
- Take DG E-Detective for service differentiation and revenue growth by user behavior data
- Imperatives to manage unwanted traffic in the networks, as well as spiraling volumes of wanted traffic – a new issue for mobile operators
- Maintain Common IT Security Standard through the Entire Organization
- Can be integrated with Auditing Tool of Central Bank
- Easy Deployment and Maintenance
|
|
|
|
|