The solution for prevention from internal threats on the network forensic technology side is gradually accepted by CIO of large enterprise, because network forensic technology solution can scan the meaningful content inside all payload of data packets. It will be easy for CIO or CISO to tell different level of IT security risk in company with such network forensic tools and prevent it happened.
In order to effectively monitor network activities, network forensic tool always comes with multiple deployments in different network segments and is managed separately by nature. So, after deployment with network forensic tools the major challenge of CIO or CISO in large enterprises is to face how to consolidate all the network forensic tools in different sites with centralized management and data retention management system.
The requirement is quite similar with the system of NVR server and multiple networked CCTV’s. In the back room, there must be a centralized management system linked with multiple network forensic systems in the frontend for system maintenance, data management, user activity management, authority and security control…etc.
On the other hand, intercepted data from each network forensic system should be also moved to central retention storage system day by day. Due to sensitivity and confidentiality of intercepted data, it should be kept in centralized site safely for further analysis no matter where it comes from. This procedure should be controlled and monitored by centralized management system.
In most enterprises with deployment of network forensic tool, the entire system from frontend probes to backend centralized and data retention management servers is all in a secured VPN network segment for corporate authorized security personnel. In the mean time, this system could also be part of IT security management (ITSM) facilities with compliance of ISO 27000 or other state mandates. All intercepted data can be the base for employee behavior pattern analysis in order to improve the corporate network and IT resource allocation.
The typical deployment of network forensic tools with centralized management system and data retention system is just like below:
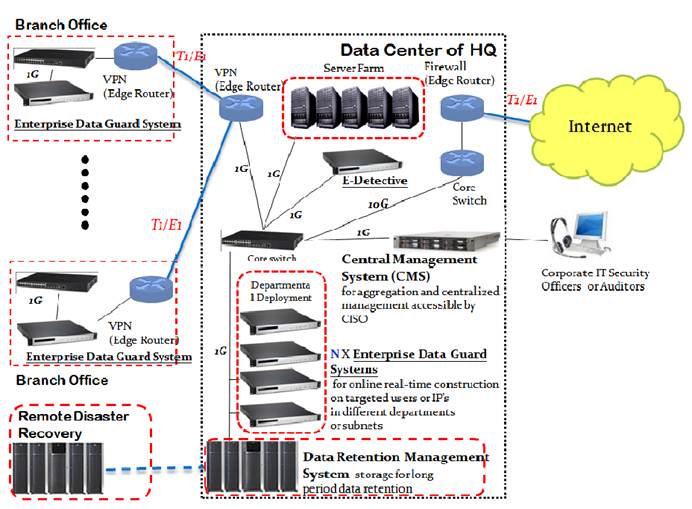
In the above figure, it is shown the frontend network forensic tools: E-Detective (ED), which is for internet monitor against internal threats, and Enterprise Data Guard System (EDGS), which is for intranet auditing with database, email and file servers. Corporate ITSO and auditor can monitor network activities and conduct data analysis through centralized management system and data retention management system. By this way, the corporate network can be completely under auditing by IT governance principles.
“I saw that lots of enterprises deploy different IT security systems, such as intrusion defensive and prevention system, email spam, firewall…etc, against malice network behavior, but there are still lots of damage by IT security threats in these companies.” said Casper Chang, CEO of Decision Group “I decided to develop an effective solution for those enterprises suffering such IT security threats 5 years ago. Now I am so glad that there are hundreds of enterprises protected by Decision Group total solutions with the least IT loss.”
Decision Group provides total integrated solutions of E-Detective and Enterprise Data Guard System with Centralized management system and data retention management system to protect the entire corporate network covering main buildings and branch offices in different places. This solution has been adopted by different departments of government of several countries, and several state finance companies in Far Eastern and ASEAN countries for more than 3 years. Decision Group solution has been proven to be the best solution for internal IT security management and auditing in the world.
“We are still working for more advanced functions in mobile environment for corporate customers with BYOD policy and provide effective data linkage analysis. I deeply hope that corporate customers can be free from network and IT threats by Decision Group solutions one day.” said Casper Chang.
About Decision Group
Decision Group, established in 1986, is one of the leaders in manufacturing of PC-Based Multi-Port RS232/422/425 Serial Cards, Data Acquisition, Measurement Products, Industrial Automation and Control Systems. Decision Group, from the year 2000, started new line of industry involved in designing and development of equipment and software for Internet Surveillance and Forensics Analysis Solutions.
Decision Group also provides OEM/ODM services of its network forensic solution with deep packet inspection (DPI) technology to other partners worldwide. Decision Group has also developed a comprehensive training course, known as Network Packet Forensics Analysis Training (NPFAT), and has set up training centers worldwide for hands-on training, with certification option as well.
More Information and Contact by Email: decision@decision.com.tw
URL: www.edecision4u.com (Global), www.internet-recordor.com.tw (Taiwan), www.god-eyes.cn (China), www.decisionjapan.com (Japan) , www.decision-groups.com (Singapore), www.e-detective.de (Germany), www.edecision4u.fr (France), www.edecision4u.es (Spain and Latin America) |