HTTPS/SSL Network Packet Forensics Device - HTTPS/SSL Real-Time Forensics and Lawful Interception System
HTTPS/SSL Network Forensics Device
(HTTPS/SSL Interceptor) is designed for Network Forensics decrypt HTTPS/SSL traffic. It is used by legal enforcement bodies, police, investigation units, forensics firms, and government departments for tracking or monitoring a suspect’s HTTP and HTTPS activities through the Internet. The HTTPS/SSL Device has Decision Group’s E-Detective web reconstruction function (HTTP Link and HTTP Content) integrated into the system which allows an administrator to see the content of normal and secured webpages.
HTTPS/SSL Interceptor operates in two modes: 1. Man in the Middle Attack (MITM); and 2. Offline Method (Decrypting HTTPS raw data with Private Key Available). In MITM method, the HTTPS/SSL Interceptor acts as a proxy to the targeted PC/suspect. All traffic from the targeted PC or suspect will be redirected to the HTTPS/SSL Interceptor. The HTTPS/SSL Interceptor will collect the genuine certificate from the SSL Server if the targeted PC accesses the SSL Server. The HTTPS/SSL Interceptor then returns its own generated certificate. Using this method, HTTPS/SSL Interceptor can decrypt the HTTPS traffic. In Offline mode, the HTTPS/SSL Interceptor is capable decrypting previously captured HTTPS raw data of decrypting if the private key is available.
Login usernames and passwords like Google or Gmail login, Yahoo Mail
login, ebay login etc. can be captured by the HTTPS/SSL
Interceptor.
Login usernames and passwords like Google or Gmail login, Yahoo Mail login, ebay logi,n etc. can also be captured by the HTTPS/SSL Interceptor.
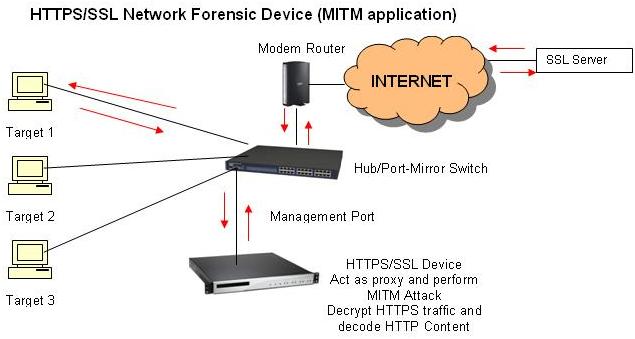
Diagram1: HTTPS/SSL
Network Packet Forensics Device MITM Implementation
More HTTPS/SSL Interceptor Product Information
|