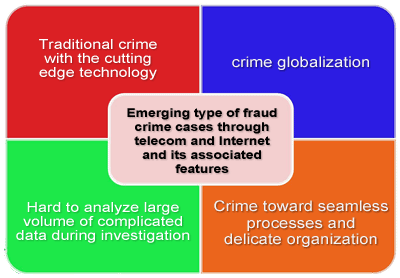
1. Fraud Crime Cases through Telecom and Internet
 |
|---|
I. Traditional Crime with Cutting Edge Technology
 |
|---|
With mobile, Internet, IP phone, mobile Internet access or other value-added telecom services, swindlers commit more crimes easily; However, by whatever advanced technology and tool they use, the nature of their crimes always stays all the same. We still need to profile such crimes by the analysis on conditions, mindset, and behavior of crime.
II. crime globalization
As applications and services of telecom technology and Internet are developing rapidly and pervasively, people are also familiar with those services. Fraud crimes through telecom and Internet, which are just like contagious diseases, may widespread globally by networks.
Globalized Crime Issue
Borderless Internet makes crime behavior more globalized. Through the Internet and cloud computing, communication in swindler group can be enhanced and anonymous. Because of limitation of state authority and anonymity, it is really hard for state prosecutors and police to take investigation on the entire crime activities.
 |
|---|
|
Cloud Computing = Network Computing |
|---|
III. Hard to analyze large volume of complicated data
There is often large volume of data or information (such as phone multiple transfers) produced by telecom and Internet fraud crimes because of converged IT network and telecom routes. In reality, such huge amount of data is acquired from multiple service providers. Investigators must apply multiple orders from court in advance to connect with data from those service providers.
(for example: If there is phone transfer between 2 operators, investigator must request both to provide CDR information and call content by 2 orders from court ahead of time, and integrate all information for further analysis.)
Therefore, it is no way to cope with such telecom and Internet fraud crime only by tradition way of comparing, claiming or tracing targets manually. It is the best way for investigator to adopt several effective software tools to analyze such huge amount of data.
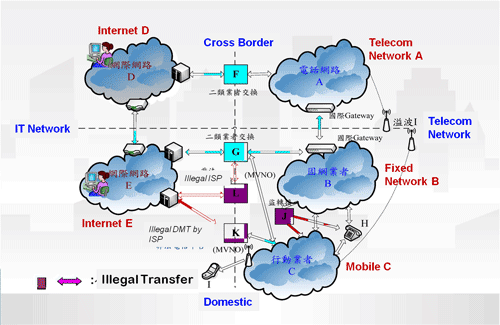 Converged ICT Communication Routes |
|---|
V. Crime toward seamless processes and delicate organization
|
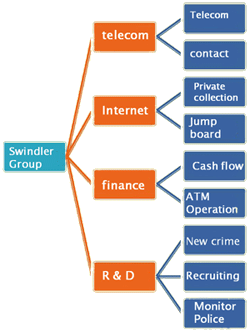
It is a nature trend that group crime is toward seamless process and delicate organization. There is very clear hierarchy of role and responsibility (R&R) for leader, telecom engineer and service staff in crime group. They never mix the use of phones for crime and private, and adopt one-way contact in order not to be cracked with whole group. Such crime model can be easily duplicated. Fraud crime group often splits into small ones, forms new gang, commits more crimes, and exchanges information and new techniques of fraud. |
 |
|---|
|
Common Features |
|---|
 |
|---|