4. Case Study of the Recent Investigation on Cyber Crimes
Lessons and Experience
Real Case on VOIP Investigation
Problem Here:
The most common tool by swindler group is telephone. While arriving the telecom room of criminal, sometimes police can’t do anything because they know nothing about these equipments and can’t track IP phone source from Internet.
 |
|---|
What to Check from Swindler Computers
- Group and Billing Systems
- Account information in SIP Gateway or IP-PBX Servers
- Detail CDR from SIP Gateway or IP-PBX Servers
VOIP Tracking from Swindler Group – Group and Billing System
 |
|---|
VOIP Gateway Investigation from Swindler group- Track SIP Server
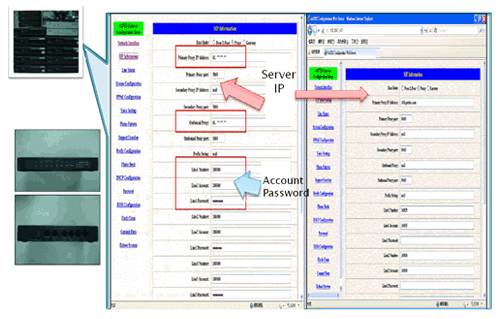 |
|---|
VOIP Tracking from Operator – CDR of SIP Server
 |
|---|
Key Points of Investigation
- Aggressively hunting for intelligence
- Don’t give up any follow-up opportunities, and carefully analyze any useful information
- Active Lawful Intercept:tap into suspected lines, intercept phone number and IMEI, phones in China, interview resident houses, and clarify criminal organization, identity and location
Experience
- familiar with law and regulations, understand what the target is and what the key evidence is. For example: find Chinese victim information and testimony through cooperation with Chinese Police after breaking cross-strait swindler group in Taiwan. Otherwise, these criminal will be non-prosecuted or non-guilty sentence by court.
- Telecom equipment supplier, telecom shop, network engineer, telecom engineer, telecom sales …network and telecom professionals usually are aware of information and location of suspects.
- Understand calling flow, and accounts of swindler group from operators side in order to find more background information from CRM and billing systems
- Active Lawful Intercept:Tap into suspected lines, intercept phone numbers to China
- Carefully Trail down: Prepare information (Time, place, behavior) in advance, trail by segment (not to expose self), identify criminal from different sides
- Use confiscated computers for investigation to find more strong evidence