iMonitor
 
The iMonitor is a powerful Lawful Interception solution that operates as the backend system in the Law Enforcement Agency’s Monitor Center to decode and reconstruct the communications traffic received from the telecom service provider’s mediation system. The iMonitor receives communication data records and communication contents from the mediation system. The iMonitor physically operates with the telecom service provider’s mediation system for intercepted data management in order to protect the confidentiality of the intercepted data and ensures that only the court-approved Law Enforcement Agent can access the communication content.
Development of IP Technology and Lawful Interception on Internet Access
To fulfill state LI mandate, it is obliged for all internet access service providers (ISP) to transmit data packets (communication content) and access log (communication information) of target subscribers to the remote monitoring facility of law enforcement agency (LEA). For such process, ETSI defines the handover interface for the data delivery from ISP to the law enforcement monitoring facility (shortly called LEMF).
However, the crime investigation practice on IP data interception is beyond that, the investigator has to do forensic jobs on the collected data, IP packets, and identify the meaningful clues from huge data is another big challenge. Without the appropriate solution, LI on IP packets can help little on crime investigation neither for homeland security.
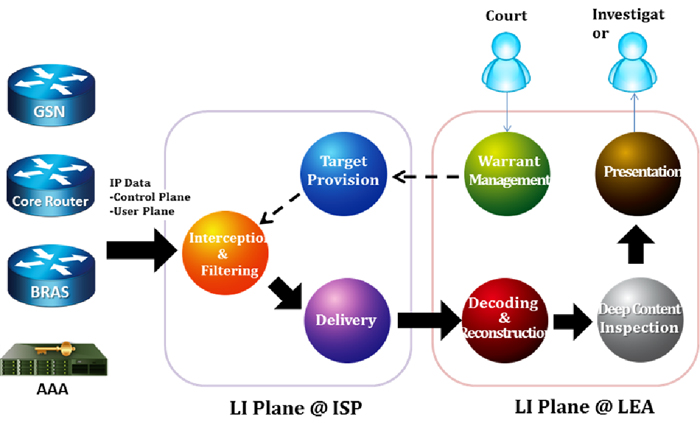
Solution from Decision Group: iMonitor
DG provides the monitoring center solution for law enforcement agency: iMonitor, which is a centralized ETSI-compliant LEMF system with several advanced post-interception analysis to fulfill crime investigation process. The major features are as below:
-Connect Multiple ISP(mediation device)
iMonitoring system locates in LEA site as the LEMF defined by ETSI standard and is able to monitor several ISPs simultaneously.
-Warrant Management
The LI target can be an ISP account or an IP address or a 3G MSISDN (phone number)…Warrant management system is to manage the life cycle of the warrants and execute the target provision and target removal by synching the warrant information to mediation devices in ISPs. In the same time, it keeps each warrant have its independent working space.
-Intercepted data forensics: protocol decoding and reconstruction
There are two types of collected data:
IRI: describes the session context information from ISP control plane for the specific targets.
CC: the IP packets intercepted from ISP user plane which are related to the specific targets.
Regarding to ETSI standard, the monitoring facility has to correlate the IRI and CC by targets. Unfortunately, only network forensics professionals can “understand” CC. For this gap, the heart of iMonitor is protocol decoding and reconstruction engine: generating the human-readable content by different protocol from those IP packets. Moreover, iMonitor presents the content on web server so that it can easily serve many users through IP network.
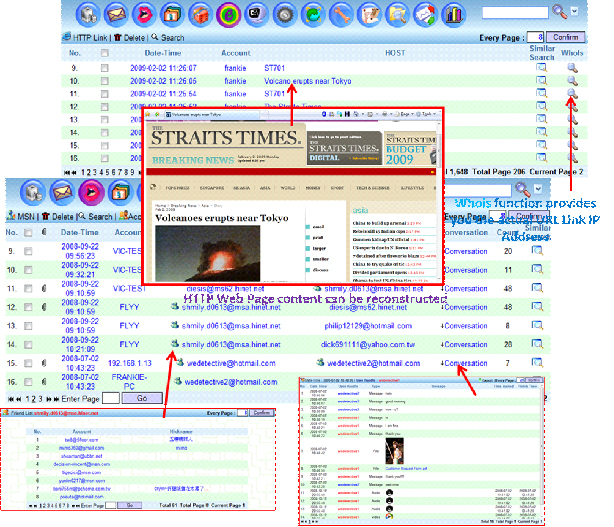
-Deep Content Inspection
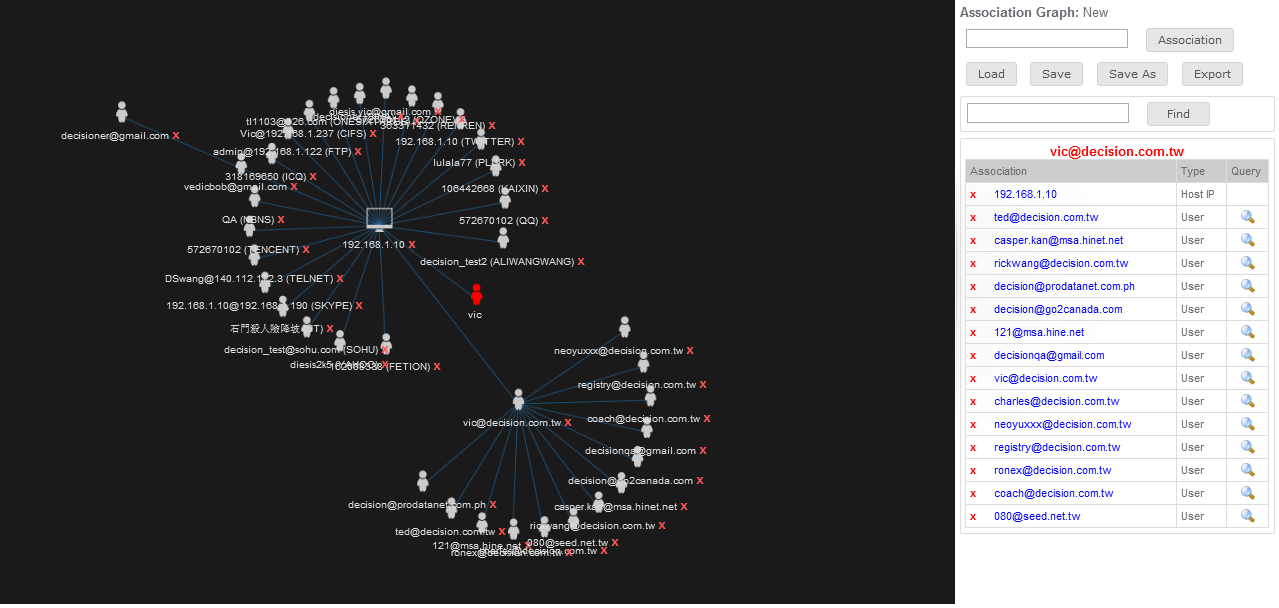
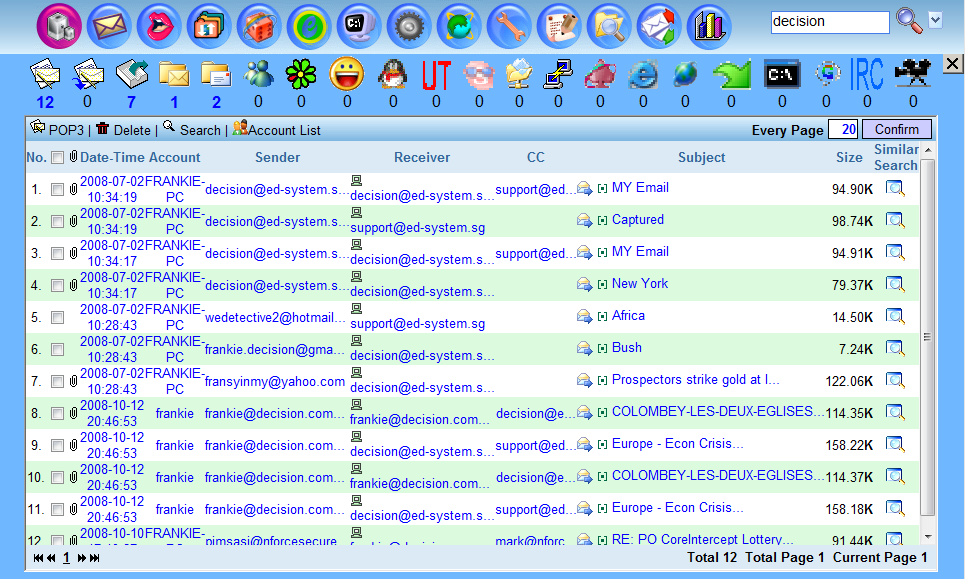
iMonitor provides the most powerful tool to search data by user-defined criteria. Moreover, the visual link analysis is provided to identify the communication relation in cyber world and even trace to the physical identity such as 3G Phone number or ISP account.
|