|
Introduction of Communication Protection and Interception Act in Taiwan, R.O.C.
Jackie Chien Cybercrime Unit of MJIB |
|
|
|
 |
Education |
|
- Master, department of Information Management of National Taipei University
- PhD student, department of law of National Chung-Cheng University
|
 |
Legal proceeding |
|
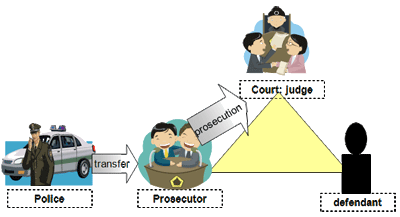 |
 |
Judicial system |
|
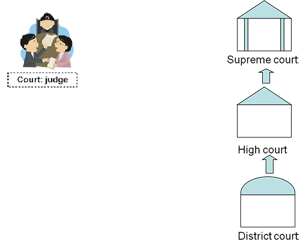 |
 |
Lawful Interception in LEA |
| |
- Interception on Voice Phone and FAX
- Network Interception
|
|
 |
 |
US Carnivore System |
|
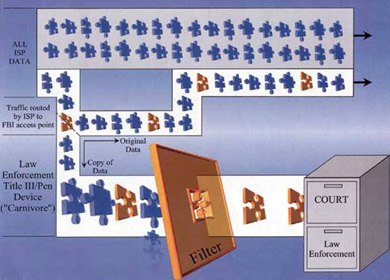 |
 |
Types of Interception |
|
 |
 |
Physical Interception & Privacy Expectation |
|
Limit to the communication, of which content with reasonable expectation of privacy and secret should be based on legal evidence |
|
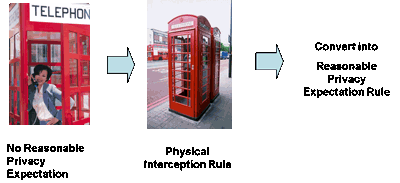 |
 |
What is Communication |
|
- Send, Storage, Transmit or Receive Symbol, Text, Video, Voice and Messages by Telecom Equipment and Other Wired or Wireless Devices
- Mail & Document
- Speech & Talking
|
 |
Types of Lawful Interception |
|
- Crime Interception
- Heavy Crime:Crime of 3-year above Sentence in Prison or Specific Ones
- Emergent Lawful Interception
- Official Approval:Issued by Judge since July 2007
- Intelligence Interception
- Collect Necessary Information from foreign Countries or hostile organizations outside country
- Official Approval:Issued by Commander of National Intelligence Organization
|
 |
Not in Private Residence |
|
- The Ways of Interception should be Interception, Eavesdrop, Voice or Video Recording, Photo, Mail-opening, Investigation, Xerox or Other Necessary Similar Methods
- No Eavesdrop Device, Video Recorder and other Interception Equipments in Private Residence Site
|
 |
Notice of Ending Interception |
|
- Procedure
- List the Name of Interceptee, Residence Site
- Report to Prosecutor, or National Intelligence Oraganization
- Submit to Court for Notice to Interceptee
- Concern
- Unless Impact to Lawful Interception or Unable to Contact, Court Should Send Notice to Interceptee
|
 |
Un-Lawful Interception |
|
- 5-year below Sentence in Prison for un-Lawful Interception
- Officers or telecom employees may be 6-month above & 5-year below sentence in prison for un-lawful interception by unauthorized empowerment
- 1-year above and 7-year below sentence in prison with the above crime for business
|
 |
Legal Lawful Interception |
|
- All by Law
- All staff of telecom or post agencies should follow regulations or related law of telecom and post services to do it
- Interceptor is one of communication parties or Pre-approval by one of communication parties, and the act must be for legal purpose
|
 |
Can your Boss Intercept Your Email? |
|
 |
 |
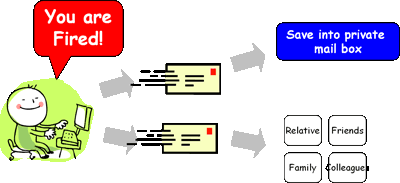
Case Study |
|
 |
 |
How Employee Responds? |
|
 |
 |
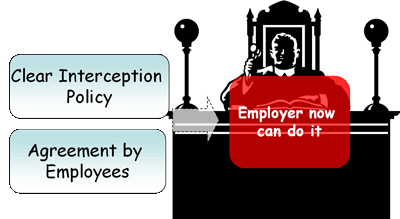
How not to Violet Employee Privacy? |
|
 |
|
|
|
|