|
E-Detective Data Guard System (Real-Time)
Unauthorized internal/external data access and attacks to an organization’s internal file servers or database system has become a very common issue today. Today, staff in organizations can easily access information shared in the organization’s networks, including the Database (customer information/vendor information etc.) and internal confidential/non-confidential files stored within the internal network (usually at the Server Farm). We can read about cases of customer information stolen by internal staff in banks, financial organizations, or government organizations and selling this information to competitors or other parties who can profit in this market. We experience it ourselves as well when we pick up calls from banks or credit card companies with which we have never had any relationship and who ask us to subscribe to their services. All these are serious issues in all organizations that do not have sufficient protections in their internal Database and File Servers systems.
E-Detective Data Guard System is used for monitoring and logging all access and activities to internal Databases (MS SQL, MySQL, Oracle DB etc.), CIFS file servers, local email servers (POP3/SMTP/IMAP), Webmail (Zimbra Mail), FTP servers, etc. within the organization’s network. It also includes alert and notification functions which allow the Administrator to be alerted if a certain pre-configured condition is matched and triggered. It also has full range search and query capability, and a range of reporting functions. With the E-Detective Data Guard System, sensitive information will not be accessed without the administrator’s knowledge.
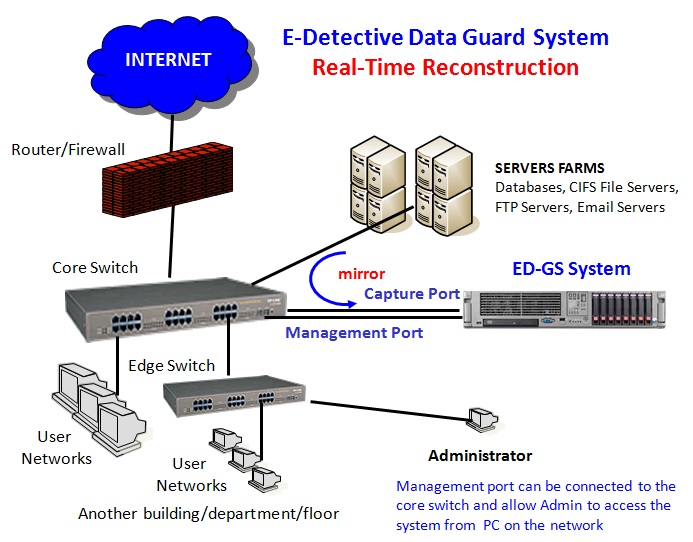
Diagram: E-Detective Data Guard System Mirror Mode Implementation - Organization Intranet Traffic Monitoring
More ED-GS Product Information |